Msc(IT)_Unit_1(Introduction to Web)_Internet and web Technology(1310505)
What is computer
networking?
Computer networking
refers to interconnected computing devices that can exchange data and share
resources with each other. These networked devices use a system of rules,
called communications protocols, to transmit information over physical or
wireless technologies.
Network computer devices that originate, route and terminate the
data are called network nodes.[1]Nodes can include hosts such as personal computers, phones,servers as well as networking hardware. Two such devices can be said to be
networked together when one device is able to exchange information with the
other device, whether or not they have a direct connection to each other.
Computer networks differ in the transmission medium used to carry their signals,
the communications
protocols to
organize network traffic, the network’s size, topology and organizational intent.
Computer networks support an enormous number of applications and services such as access to the World Wide Web, digital video, digital audio, shared use of application and storage servers, printers, and fax
machines, and
use of email and instant messaging applications as well as many others. In most cases,
application-specific communications protocols are layered (i.e. carried as payload) over other more general communications
protocols.
Computer network design falls under two broad categories:
1. Client-server architecture
In this type of computer network, nodes may be servers or
clients. Server nodes provide resources like memory, processing power, or data
to client nodes. Server nodes may also manage client node behavior. Clients may
communicate with each other, but they do not share resources. For example, some
computer devices in enterprise networks store data and configuration settings.
These devices are the servers in the network. Clients may access this data by
making a request to the server machine.
What is a Client?
A client is a computer hardware
device or software that accesses a service made available by a server. The
server is often (but not always) located on a separate physical computer.
What is a Server? A server is a physical computer dedicated to run services to serve
the needs of other computers. Depending on the service that is running, it
could be a file server, database server, home media server, print server, or
web server.
2. Peer-to-peer
architecture
In Peer-to-Peer (P2P) architecture, connected computers have
equal powers and privileges. There is no central server for coordination. Each
device in the computer network can act as either client or server. Each peer
may share some of its resources, like memory and processing power, with the
entire computer network. For example, some companies use P2P architecture to
host memory-consuming applications, such as 3-D graphic rendering, across
multiple digital devices.
Computer Network Types
A computer network is a group
of computers linked to each other that enables the computer to communicate with
another computer and share their resources, data, and applications.
A computer network can be
categorized by their size. A computer network is
mainly of four types:
- LAN(Local
Area Network)
- PAN(Personal
Area Network)
- MAN(Metropolitan
Area Network)
- WAN(Wide
Area Network)
LAN(Local Area Network)
- Local
Area Network is a group of computers connected to each other in a small
area such as building, office.
- LAN
is used for connecting two or more personal computers through a
communication medium such as twisted pair, coaxial cable, etc.
- It
is less costly as it is built with inexpensive hardware such as hubs,
network adapters, and ethernet cables.
- The
data is transferred at an extremely faster rate in Local Area Network.
- Local
Area Network provides higher security.
PAN(Personal Area Network)
- Personal
Area Network is a network arranged within an individual person, typically
within a range of 10 meters.
- Personal
Area Network is used for connecting the computer devices of personal use
is known as Personal Area Network.
- Personal
Area Network covers an area of 30
feet.
- Personal
computer devices that are used to develop the personal area network are
the laptop, mobile phones, media player and play stations.
There are two types of Personal Area Network:
- Wired
Personal Area Network
- Wireless
Personal Area Network
Wireless Personal Area Network: Wireless Personal
Area Network is developed by simply using wireless technologies such as WiFi,
Bluetooth. It is a low range network.
Wired Personal Area Network: Wired Personal
Area Network is created by using the USB.
Examples
Of Personal Area Network:
- Body Area Network: Body Area Network is a
network that moves with a person. For example, a mobile network moves
with a person. Suppose a person establishes a network connection and then
creates a connection with another device to share the information.
- Offline Network: An offline network can be
created inside the home, so it is also known as a home network. A
home network is designed to integrate the devices such as printers,
computer, television but they are not connected to the internet.
- Small Home Office: It is used to connect a
variety of devices to the internet and to a corporate network using a VPN
MAN(Metropolitan Area Network)
- A
metropolitan area network is a network that covers a larger geographic
area by interconnecting a different LAN to form a larger network.
- Government
agencies use MAN to connect to the citizens and private industries.
- In
MAN, various LANs are connected to each other through a telephone exchange
line.
- The
most widely used protocols in MAN are RS-232, Frame Relay, ATM, ISDN,
OC-3, ADSL, etc.
- It
has a higher range than local area network(LAN)
- MAN
is used in communication between the banks in a city.
- It
can be used in an Airline Reservation.
- It
can be used in a college within a city.
- It
can also be used for communication in the military.
WAN(Wide Area Network)
- A
Wide Area Network is a network that extends over a large geographical area
such as states or countries.
- A
Wide Area Network is quite bigger network than the LAN.
- A
Wide Area Network is not limited to a single location, but it spans over a
large geographical area through a telephone line, fibre optic cable or
satellite links.
- The
internet is one of the biggest WAN in the world.
- A
Wide Area Network is widely used in the field of Business, government, and
education.
Examples
Of Wide Area Network:
- Mobile Broadband: A 4G network is widely
used across a region or country.
- Private network: A bank provides a private
network that connects the 44 offices. This network is made by using the
telephone leased line provided by the telecom company.
Advantages
Of Wide Area Network:
Following are the advantages of the Wide Area Network:
- Geographical area: A Wide Area Network
provides a large geographical area. Suppose if the branch of our office is
in a different city then we can connect with them through WAN. The
internet provides a leased line through which we can connect with another
branch.
- Centralized data: In case of WAN network,
data is centralized. Therefore, we do not need to buy the emails, files or
back up servers.
- Get updated files: Software companies work on
the live server. Therefore, the programmers get the updated files within
seconds.
- Exchange messages: In a WAN network, messages
are transmitted fast. The web application like Facebook, Whatsapp, Skype
allows you to communicate with friends.
- Sharing of software and resources: In WAN network, we can
share the software and other resources like a hard drive, RAM.
- Global business: We can do the business
over the internet globally.
- High bandwidth: If we use the leased lines
for our company then this gives the high bandwidth. The high bandwidth
increases the data transfer rate which in turn increases the productivity
of our company.
Disadvantages
of Wide Area Network:
The following are the disadvantages of the Wide Area Network:
- Security issue: A WAN network has more
security issues as compared to LAN and MAN network as all the technologies
are combined together that creates the security problem.
- Needs Firewall & antivirus software: The data is transferred on
the internet which can be changed or hacked by the hackers, so the
firewall needs to be used. Some people can inject the virus in our system
so antivirus is needed to protect from such a virus.
- High Setup cost: An installation cost of
the WAN network is high as it involves the purchasing of routers,
switches.
- Troubleshooting problems: It covers a large area so
fixing the problem is difficult.
Types of Network Topology
The arrangement of a network that comprises nodes and connecting lines via sender and receiver is referred to as Network Topology. The various network topologies are:
- Point to Point Topology
- Mesh Topology
- Star Topology
- Bus Topology
- Ring Topology
- Tree Topology
Point to Point Topology
Point-to-Point Topology is a type of topology that works on the functionality of the sender and receiver. It is the simplest communication between two nodes, in which one is the sender and the other one is the receiver. Point-to-Point provides high bandwidth.
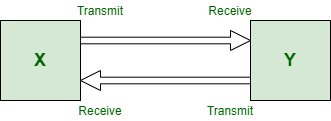
Point to Point Topology

Point to Point Topology
Mesh Topology
In a mesh topology, every device is connected to another device via a particular channel. In Mesh Topology, the protocols used are AHCP (Ad Hoc Configuration Protocols), DHCP (Dynamic Host Configuration Protocol), etc.
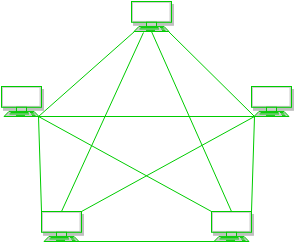
Mesh Topology
Figure 1: Every device is connected to another via dedicated channels. These channels are known as links.
- Suppose, the N number of devices are connected with each other in a mesh topology, the total number of ports that are required by each device is N-1. In Figure 1, there are 5 devices connected to each other, hence the total number of ports required by each device is 4. The total number of ports required = N * (N-1).
- Suppose, N number of devices are connected with each other in a mesh topology, then the total number of dedicated links required to connect them is NC2 i.e. N(N-1)/2. In Figure 1, there are 5 devices connected to each other, hence the total number of links required is 5*4/2 = 10.
Advantages of Mesh Topology
- Communication is very fast between the nodes.
- Mesh Topology is robust.
- The fault is diagnosed easily. Data is reliable because data is transferred among the devices through dedicated channels or links.
- Provides security and privacy.
Drawbacks of Mesh Topology
- Installation and configuration are difficult.
- The cost of cables is high as bulk wiring is required, hence suitable for less number of devices.
- The cost of maintenance is high.
A common example of mesh topology is the internet backbone, where various internet service providers are connected to each other via dedicated channels. This topology is also used in military communication systems and aircraft navigation systems.

Mesh Topology
Star Topology
In Star Topology, all the devices are connected to a single hub through a cable. This hub is the central node and all other nodes are connected to the central node. The hub can be passive in nature i.e., not an intelligent hub such as broadcasting devices, at the same time the hub can be intelligent known as an active hub. Active hubs have repeaters in them. Coaxial cables or RJ-45 cables are used to connect the computers. In Star Topology, many popular Ethernet LAN protocols are used as CD(Collision Detection), CSMA (Carrier Sense Multiple Access), etc.

Star Topology
Figure 2: A star topology having four systems connected to a single point of connection i.e. hub.
Advantages of Star Topology
- If N devices are connected to each other in a star topology, then the number of cables required to connect them is N. So, it is easy to set up.
- Each device requires only 1 port i.e. to connect to the hub, therefore the total number of ports required is N.
- It is Robust. If one link fails only that link will affect and not other than that.
- Easy to fault identification and fault isolation.
- Star topology is cost-effective as it uses inexpensive coaxial cable.
Drawbacks of Star Topology
- If the concentrator (hub) on which the whole topology relies fails, the whole system will crash down.
- The cost of installation is high.
- Performance is based on the single concentrator i.e. hub.
A common example of star topology is a local area network (LAN) in an office where all computers are connected to a central hub. This topology is also used in wireless networks where all devices are connected to a wireless access point.

Star Topology
Bus Topology
Bus Topology is a network type in which every computer and network device is connected to a single cable. It is bi-directional. It is a multi-point connection and a non-robust topology because if the backbone fails the topology crashes. In Bus Topology, various MAC (Media Access Control) protocols are followed by LAN ethernet connections like TDMA, Pure Aloha, CDMA, Slotted Aloha, etc.
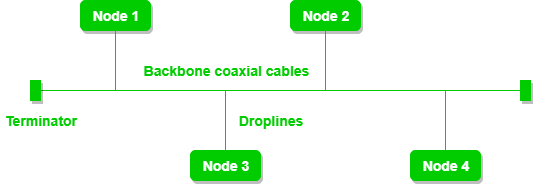
Bus Topology
Figure 3: A bus topology with shared backbone cable. The nodes are connected to the channel via drop lines.
Advantages of Bus Topology
- If N devices are connected to each other in a bus topology, then the number of cables required to connect them is 1, known as backbone cable, and N drop lines are required.
- Coaxial or twisted pair cables are mainly used in bus-based networks that support up to 10 Mbps.
- The cost of the cable is less compared to other topologies, but it is used to build small networks.
- Bus topology is familiar technology as installation and troubleshooting techniques are well known.
- CSMA is the most common method for this type of topology.
Drawbacks of Bus Topology
- A bus topology is quite simpler, but still, it requires a lot of cabling.
- If the common cable fails, then the whole system will crash down.
- If the network traffic is heavy, it increases collisions in the network. To avoid this, various protocols are used in the MAC layer known as Pure Aloha, Slotted Aloha, CSMA/CD, etc.
- Adding new devices to the network would slow down networks.
- Security is very low.
A common example of bus topology is the Ethernet LAN, where all devices are connected to a single coaxial cable or twisted pair cable. This topology is also used in cable television networks.

Bus Topology
Ring Topology
In a Ring Topology, it forms a ring connecting devices with exactly two neighboring devices. A number of repeaters are used for Ring topology with a large number of nodes, because if someone wants to send some data to the last node in the ring topology with 100 nodes, then the data will have to pass through 99 nodes to reach the 100th node. Hence to prevent data loss repeaters are used in the network.
The data flows in one direction, i.e. it is unidirectional, but it can be made bidirectional by having 2 connections between each Network Node, it is called Dual Ring Topology. In-Ring Topology, the Token Ring Passing protocol is used by the workstations to transmit the data.
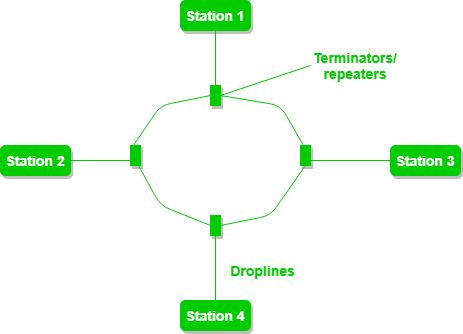
Ring Topology
Figure 4: A ring topology comprises 4 stations connected with each forming a ring.
The most common access method of ring topology is token passing.
- Token passing: It is a network access method in which a token is passed from one node to another node.
- Token: It is a frame that circulates around the network.
Operations of Ring Topology
- One station is known as a monitor station which takes all the responsibility for performing the operations.
- To transmit the data, the station has to hold the token. After the transmission is done, the token is to be released for other stations to use.
- When no station is transmitting the data, then the token will circulate in the ring.
- There are two types of token release techniques: Early token release releases the token just after transmitting the data and Delayed token release releases the token after the acknowledgment is received from the receiver.
Advantages of Ring Topology
- The data transmission is high-speed.
- The possibility of collision is minimum in this type of topology.
- Cheap to install and expand.
- It is less costly than a star topology.
Drawbacks of Ring Topology
- The failure of a single node in the network can cause the entire network to fail.
- Troubleshooting is difficult in this topology.
- The addition of stations in between or the removal of stations can disturb the whole topology.
- Less secure.

Ring Topology
Tree Topology
This topology is the variation of the Star topology. This topology has a hierarchical flow of data. In Tree Topology, protocols like DHCP and SAC (Standard Automatic Configuration ) are used.

Tree Topology
Figure 5: In this, the various secondary hubs are connected to the central hub which contains the repeater. This data flow from top to bottom i.e. from the central hub to the secondary and then to the devices or from bottom to top i.e. devices to the secondary hub and then to the central hub. It is a multi-point connection and a non-robust topology because if the backbone fails the topology crashes.
Advantages of Tree Topology
- It allows more devices to be attached to a single central hub thus it decreases the distance that is traveled by the signal to come to the devices.
- It allows the network to get isolated and also prioritize from different computers.
- We can add new devices to the existing network.
- Error detection and error correction are very easy in a tree topology.
Drawbacks of Tree Topology
- If the central hub gets fails the entire system fails.
- The cost is high because of the cabling.
- If new devices are added, it becomes difficult to reconfigure.
A common example of a tree topology is the hierarchy in a large organization. At the top of the tree is the CEO, who is connected to the different departments or divisions (child nodes) of the company. Each department has its own hierarchy, with managers overseeing different teams (grandchild nodes). The team members (leaf nodes) are at the bottom of the hierarchy, connected to their respective managers and departments.

Tree Topology
ISP: Internet Service Provider
ISP stands for Internet Service Provider. It is a company that
provides access to the internet and similar services such as Website designing
and virtual hosting. For example, when you connect to the Internet, the
connection between your Internet-enabled device and the internet is executed
through a specific transmission technology that involves the transfer of
information packets through an Internet Protocol route.
Data is transmitted through
different technologies, including cable modem, dial-up, DSL, high speed
interconnects. Accordingly, based on the method of data transmission, the
Internet access provided by ISPs can be divided into many types, some of which
are as follows:
Dial-up Internet access: It is the oldest
technology to provide Internet access by modem to modem connection using
telephone lines. In this method, the user's computer is connected to a modem
with a telephone line. This method has become outdated today due to slow
connection speed. However, in remote areas, this method can be used where the
broadband network is not available.
DSL: DSL, which stands for 'digital subscriber line' is an
advanced version of the dial-up Internet access method. It uses high frequency
to execute a connection over the telephone network and allows the internet and
the phone connection to run on the same telephone line. This method offers an
Asymmetric Digital Subscriber (ADSL), where the upload speed is less than the
download speed, and a Symmetric Digital Subscriber Line (SDSL), which offers
equal upload and download speeds. Out of these two, ADSL is more popular among
users and is popularly known as DSL.
Wireless Broadband (WiBB): It is a modern
broadband technology for Internet access. It allows high-speed wireless
internet within a large area. To use this technology, you are required to place
a dish on the top of your house and point it to the transmitter of your
Wireless Internet Service Provider (WISP).
Wi-Fi Internet: It is the short
form for "wireless fidelity," which is a wireless networking
technology that provides wireless high-speed Internet connections using radio
waves. To use the internet, you are required to be within the range of wi-fi
network. It is commonly used in public places such as hotels, airports,
restaurants to provide internet access to customers.
ISDN: It is a short form of Integrated
Services Digital Network. It is a telephone system network which integrates a
high-quality digital transmission of voice and data over the same standard
phone line. It offers a fast upstream and downstream Internet connection speed
and allows both voice calls and data transfer.
Ethernet: It is a wired LAN (Local Area
Network) where computers are connected within a primary physical space. It
enables devices to communicate with each other via a protocol (a set of rules
or common network language). It may provide different speeds such as 10 Mbps,
100 Mbps and 10 Gbp.
Internetwork
- An internetwork is defined as two or
more computer network LANs or WAN or computer network segments are
connected using devices, and they are configured by a local addressing
scheme. This process is known as internetworking.
- An interconnection between public,
private, commercial, industrial, or government computer networks can also
be defined as internetworking.
- An internetworking uses the internet
protocol.
- The reference model used for
internetworking is Open System Interconnection(OSI).
Types Of Internetwork:
1.Internet:
An Internet is a public network and it is not owned by anyone. Since, it is a
public network therefore anyone can access it without a valid username and
password. Internet is the largest network in the case of number of connected
devices. In this, there are numerous users and it provides lots of information
to users. It acts as a tool for sharing information all over the world.
2.Extranet:
Extranet is a private network and it is owned by a single or multiple
organization. Since, it is a private network therefore no one can access it
without a valid username and password. It acts as a medium to share the information
between the internal and external members. It is more secure network and
managed by numerous organizations.
Intranet advantages:
- Communication: It provides a cheap and easy
communication. An employee of the organization can communicate with
another employee through email, chat.
- Time-saving: Information on the intranet is
shared in real time, so it is time-saving.
- Collaboration: Collaboration is one of the
most important advantage of the intranet. The information is distributed
among the employees of the organization and can only be accessed by the
authorized user.
- Platform independency: It is a neutral architecture as
the computer can be connected to another device with different
architecture.
- Cost effective: People can see the data and
documents by using the browser and distributes the duplicate copies over
the intranet. This leads to a reduction in the cost.
|
|
Internet |
|
Extranet |
|
1. |
It is
used as public network. |
Whereas
it is used as private network. |
|
|
2. |
An
internet is less secure because it has zero security level in the firewall. |
While
the extranet is more secure than the Internet. |
|
|
3. |
In the
case of the Internet, anyone can access it without a valid username and
password. |
Whereas
in the case of extranet, no one can access it without a valid username and
password. |
|
|
4. |
A large
number of users can access the Internet. |
Whereas
here, a limited number of users can access the extranet. |
|
|
5. |
An
internet acts as a tool for sharing information all over the world. |
Whereas
it acts as a medium to share the information between the internal and
external members. |
|
|
6. |
An
internet is not owned by anyone. |
Whereas
extranet is owned by a single or multiple organization. |
|
|
7. |
An
Internet is not managed by either authority. |
Unlike
the internet, it is managed by numerous organizations. |
|
|
8. |
An
internet is the largest network in the case of number of connected devices. |
Whereas
in the case of extranet, it is small in terms of connected devices as
compared to the internet. |
|
|
9. |
An
internet is less costly than extranet. |
Whereas
in the case of extranet, it is more costly. |
|
|
10. |
It’s
users are the general public. |
It’s
users are the employees of the organization which are connected. |
|
|
11. |
It is
not owned by anyone. |
It is
owned by single or multiple organization. |
|
|
12. |
There
is no regulating authority for Internet. |
It is
regulated by multiple organizations. |
|
|
13. |
It is
maintained by ISP. |
It is
maintained by CIO, HR or communication department of an organization. |
|
|
14. |
It is
the network of networks. |
It is
derived from Intranet. |
|
|
15. |
Example:
What we are normally using is Internet. |
Example:
DELL and Intel using network for business related operations. |
|
The Internet, sometimes called simply
"the Net," is a worldwide system of computer networks -- a network of
networks in which users at any one computer can, if they have permission, get
information from any other computer (and sometimes talk directly to users at
other computers). It was conceived by the Advanced Research Projects Agency
(ARPA) of the U.S. government in 1969 and was first known as the ARPANET. The
original aim was to create a network that would allow users of a research
computer at one university to "talk to" research computers at other
universities.
1. Internet :
The network formed by the co-operative interconnection of millions of computers, linked together is called Internet. Internet comprises of :
- People : People use and develop the network.
- Resources : A collection of resources that can be reached from those networks.
- A setup for collaboration : It includes the member of the research and educational committees worldwide.
2. Intranet :
It is an internal private network built within an organization using Internet and World Wide Web standards and products that allows employees of an organization to gain access to corporate information.
3. Extranet :
It is the type of network that allows users from outside to access the Intranet of an organization.
Difference between Internet, Intranet and Extranet :
| Point of difference | Internet | Intranet | Extranet |
|---|---|---|---|
| Accessibility of network | Public | Private | Private |
| Availability | Global system. | Specific to an organization. | To share information with suppliers and vendors it makes the use of public network. |
| Coverage | All over the world. | Restricted area upto an organization. | Restricted area upto an organization and some of its stakeholders or so. |
| Accessibility of content | It is accessible to everyone connected. | It is accessible only to the members of organization. | Accessible only to the members of organization and external members with logins. |
| No. of computers connected | It is largest in number of connected devices. | The minimal number of devices are connected. | The connected devices are more comparable with Intranet. |
| Owner | No one. | Single organization. | Single/ Multiple organization. |
| Purpose of the network | It’s purpose is to share information throughout the world. | It’s purpose is to share information throughout the organization. | It’s purpose is to share information between members and external, members. |
| Security | It is dependent on the user of the device connected to network. | It is enforced via firewall. | It is enforced via firewall that separates internet and extranet. |
| Users | General public. | Employees of the organization. | Employees of the organization which are connected. |
| Policies behind setup | There is no hard and fast rule for policies. | Policies of the organization are imposed. | Policies of the organization are imposed. |
| Maintenance | It is maintained by ISP. | It is maintained by CIO. HR or communication department of an organization. | It is maintained by CIO. HR or communication department of an organization. |
| Economical | It is more economical to use. | It is less economical. | It is also less economical. |
| Relation | It is the network of networks. | It is derived from Internet. | It is derived from Intranet. |
| Example | What we are normally using is internet. | WIPRO using internal network for its business operations. | DELL and Intel using network for its business operations. |
What is World Wide Web (WWW,
W3)?
--collection of text
pages,digital photograph, music files, video and animation that you can access
over internet.
The World Wide Web -- also known as the web, WWW or W3 -- refers
to all the public websites or pages that users can access on their local
computers and other devices through the internet.
These pages and documents are interconnected by means of hyperlinks that users click on for information. This information can
be in different formats, including text, images, audio and video.
The term World Wide Web isn't synonymous with
the internet. Rather, the World Wide Web is part of the internet.
How the World Wide
Web works
Paving
the way for an internet revolution that has transformed the world in only three
decades, the World Wide Web consists of multiple components that enable users
to access various resources, documents and web pages on the internet. Thus, the
WWW is like a vast electronic book whose pages are stored or hosted on
different servers worldwide.
These
pages are the primary component or building blocks of the WWW and are linked
through hyperlinks, which provide access from one specific spot in a hypertext or hypermedia document
to another spot within that document or a different one. Hyperlinks are another
defining concept of the WWW and provide its identity as a collection of
interconnected documents.
Web Page
Web page is a document available on world
wide web. Web Pages are stored on web server and can be viewed using a web
browser.
A web page
can cotain huge information including text, graphics, audio, video and hyper
links. These hyper links are the link to other web pages.
Collection of linked web pages on a web server is known as website. There
is unique Uniform Resource Locator (URL) is associated with
each web page.
Static Web page
Static
web pages are also
known as flat or stationary web page. They are loaded on the client’s browser
as exactly they are stored on the web server. Such web pages contain only
static information. User can only read the information but can’t do any
modification or interact with the information.
Static web
pages are created using only HTML. Static web pages are only used when the
information is no more required to be modified.
Dynamic Web page
Dynamic web page shows different information at different point of time. It is possible to change a portaion of a web page without loading the entire web page
What is HTTP?
The Hypertext Transfer Protocol (HTTP) is the foundation of the World Wide Web, and is used to load web pages using hypertext links. HTTP is an application layer protocol designed to transfer information between networked devices and runs on top of other layers of the network protocol stack. A typical flow over HTTP involves a client machine making a request to a server, which then sends a response message.
HTTP stands for Hypertext Transfer Protocol.
HTTP is based on the client-server architecture model and a stateless request/response
protocol that operates by exchanging messages across a reliable TCP/IP connection.
An HTTP "client" is a program (Web browser) that establishes a connection to a server for the
purpose of sending one or more HTTP request messages. An HTTP "server" is a program
(generally a web server like Apache Web Server) that accepts connections in order to serve
HTTP requests by sending HTTP response messages.
Errors on the Internet can be quite frustrating — especially if you do not know the difference
between a 404 error and a 502 error. These error messages, also called HTTP status codes are
response codes given by Web servers and help identify the cause of the problem.
For example, "404 File Not Found" is a common HTTP status code. It means the Web server
cannot find the file you requested. The file -- the webpage or other document you try to load in
your Web browser has either been moved or deleted, or you entered the wrong URL or
document name.
HTTP is a stateless protocol means the HTTP Server doesn't maintain the contextual
information about the clients communicating with it and hence we need to maintain sessions
in case we need that feature for our Web-applications
HTTP header fields provide required information about the request or response, or about the
object sent in the message body. There are four types of HTTP message headers:
o General-header:
These header fields have general applicability for both request and response messages.
o Request-header:
These header fields have applicability only for request messages.
o Response-header:
These header fields have applicability only for response messages.
o Entity-header:
These header fields define Meta information about the entity-body.
What’s in an HTTP request?
An HTTP request is the way internet communications platforms such as web browsers ask for the information they need to load a website.
Each
HTTP request made across the Internet carries with it a series of encoded data
that carries different types of information. A typical HTTP request contains:
1. HTTP
version type
2. a
URL
3. an
HTTP method
4. HTTP
request headers
5. Optional
HTTP body.
What’s an HTTP method?
An HTTP method, sometimes referred to as an HTTP verb, indicates the action that the HTTP request expects from the queried server. For example, two of the most common HTTP methods are ‘GET’ and ‘POST’; a ‘GET’ request expects information back in return (usually in the form of a website), while a ‘POST’ request typically indicates that the client is submitting information to the web server (such as form information, e.g. a submitted username and password).
| .N. | Method and Description |
|---|---|
| 1 | GET The GET method is used to retrieve information from the given server using a given URI. Requests using GET should only retrieve data and should have no other effect on the data. |
| 2 | HEAD Same as GET, but it transfers the status line and the header section only. |
| 3 | POST A POST request is used to send data to the server, for example, customer information, file upload, etc. using HTML forms. |
| 4 | PUT Replaces all the current representations of the target resource with the uploaded content. |
| 5 | DELETE Removes all the current representations of the target resource given by URI. |
HTTP request headers:
Some of the information within an HTTP request header includes:
- Source IP address and port number
- Requested URI (data or web page)
- Host (Destination website or web server)
- Type of data the browser will accept in return (text, html, xml etc)
- User’s browser type (Mozilla, Chrome, IE) so that the Web server can send compatible data.
As mentioned, whenever you enter a URL in the address box of the browser, the browser translates the URL into a request message according to the specified protocol; and sends the request message to the server.
For example, the browser translated the URL
http://www.nowhere123.com/doc/index.htmlinto the following request message:GET /docs/index.html HTTP/1.1 Host: www.nowhere123.com Accept: image/gif, image/jpeg, */* Accept-Language: en-us Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1) (blank line)
When this request message reaches the server, the server can take either one of these actions:
- The server interprets the request received, maps the request into a file under the server's document directory, and returns the file requested to the client.
- The server interprets the request received, maps the request into a program kept in the server, executes the program, and returns the output of the program to the client.
- The request cannot be satisfied, the server returns an error message.
What’s in an HTTP response?
An HTTP response is what web clients
(often browsers) receive from an Internet server in answer to an HTTP request.
These responses communicate valuable information based on what was asked for in
the HTTP request.
A typical HTTP response contains:
1.
an HTTP status code
2.
HTTP response headers
3.
optional HTTP body
Message Status-Line
A Status-Line consists of the protocol version followed by a numeric status code and its associated textual phrase. The elements are separated by space SP characters.
Status-Line = HTTP-Version SP Status-Code SP Reason-Phrase CRLF
HTTP Version
A server supporting HTTP version 1.1 will return the following version information:
HTTP-Version = HTTP/1.1
Status Code
The Status-Code element is a 3-digit integer where first digit of the Status-Code defines the class of response and the last two digits do not have any categorization role. There are 5 values for the first digit:
| S.N. | Code and Description |
|---|---|
| 1 | 1xx: Informational It means the request was received and the process is continuing. |
| 2 | 2xx: Success It means the action was successfully received, understood, and accepted. |
| 3 | 3xx: Redirection It means further action must be taken in order to complete the request. |
| 4 | 4xx: Client Error It means the request contains incorrect syntax or cannot be fulfilled. |
| 5 | 5xx: Server Error It means the server failed to fulfill an apparently valid request |
HTTP/1.1 200 OK Date: Sun, 18 Oct 2009 08:56:53 GMT Server: Apache/2.2.14 (Win32) Last-Modified: Sat, 20 Nov 2004 07:16:26 GMT ETag: "10000000565a5-2c-3e94b66c2e680" Accept-Ranges: bytes Content-Length: 44 Connection: close Content-Type: text/html X-Pad: avoid browser bug
Examples of Communication Protocols:
1.
HTTP(Hypertext transfer
protocol): It is a layer 7 protocol that is designed
for transferring a hypertext between two or more systems. HTTP works on a
client-server model, most of the data sharing over the web are done through
using HTTP.
2.
TCP(Transaction control
protocol): It lay-outs a reliable stream delivery
by using sequenced acknowledgment. It is a connection-oriented protocol i.e.,
it establishes a connection between applications before sending any data. It is
used for communicating over a network. It has many applications such as emails,
FTP, streaming media, etc.
3.
UDP(User datagram protocol): It is a connectionless protocol that lay-out a basic
but unreliable message service. It adds no flow control, reliability, or
error-recovery functions. UPD is functional in cases where reliability is not
required. It is used when we want faster transmission, for multicasting and
broadcasting connections, etc.
4.
BGP(Border gateway protocol): It is a routing protocol that controls how packets pass
through the router in an independent system one or more networks run by a
single organization and connect to different networks. It connects the
endpoints of a LAN with other LANs and it also connects endpoints in different
LANs to one another.
5.
ARP(Address Resolution
protocol): ARP is a protocol that helps in
mapping Logical addresses to the Physical addresses acknowledged in a local
network. For mapping and maintaining a correlation between these logical and
physical addresses a table known as ARP cache is used.
6.
IP(Internet Protocol): It is a protocol through which data is sent from one host
to another over the internet. It is used for addressing and routing data
packets so that they can reach their destination.
7.
DHCP(Dynamic Host Configuration
Protocol): it’s a protocol for network management
and it’s used for the method of automating the process of configuring devices
on IP networks. A DHCP server automatically assigns an IP address and various
other configurational changes to devices on a network so they can communicate
with other IP networks. it also allows devices to use various services such as
NTP, DNS, or any other protocol based on TCP or UDP.
2. Management
These protocols assist in describing the procedures and
policies that are used in monitoring, maintaining, and managing the computer
network. These protocols also help in communicating these requirements across
the network to ensure stable communication. Network management protocols can
also be used for troubleshooting connections between a host and a client.
Examples of Management Protocols:
1.
ICMP(Internet control Message protocol): It is a layer 3 protocol that is used by network devices
to forward operational information and error messages. It is used for reporting
congestions, network errors, diagnostic purposes, and timeouts.
2.
SNMP(Simple Network Management
Protocol): It is a layer 7 protocol that is used for
managing nodes on an IP network. There are three main components in SNMP
protocol i.e., SNMP agent, SNMP manager, and managed device. SNMP agent has the
local knowledge of management details, it translates those details into a form
that is compatible with the SNMP manager. The manager presents data acquired
from SNMP agents, thus helping in monitoring network glitches, network
performance, and troubleshooting them.
3.
FTP(File Transfer Protocol): FTP is a Client/server protocol that is used for
moving files to or from a host computer, it allows users to download files,
programs, web pages, and other things that are available on other services.
4.
POP3(Post office protocol): It is a protocol that a local mail client uses to get
email messages from a remote email server over a TCP/IP connection. Email
servers hosted by ISPs also use the POP3 protocol to hold and receive emails
intended for their users. Eventually, these users will use email client
software to look at their mailbox on the remote server and to download their
emails. After the email client downloads the emails, they are generally deleted
from the servers.
5.
SMTP(Simple mail transfer protocol)
6.
Telnet: It is a protocol that allows the user to connect to
a remote computer program and to use it i.e., it is designed for remote
connectivity. Telnet creates a connection between a host machine and a remote
endpoint to enable a remote session.
3. Security
These protocols secure the data in passage over a network.
These protocols also determine how the network secures data from any
unauthorized attempts to extract or review data. These protocols make sure that
no unauthorized devices, users, services can access the network data.
Primarily, these protocols depend on encryption to secure data.
Examples of Security Protocols:
1.
SSL(Secure Socket Layer): It is a network security protocol mainly used for
protecting sensitive data and securing internet connections. SSL allows both
servers to server and client to server communication. All the data transferred
through SSL is encrypted thus stopping any unauthorized person from accessing
it.
2.
HTTPS: It is the secured version of HTTP; this protocol ensures
secure communication between two computers where one sends the request through
the browser and the other fetches the data from the webserver.
3.
TSL(Transport layer security): It is a security protocol designed for data security
and privacy over the internet, its functionality is encryption, checking the
integrity of data i.e., whether it has been tampered with or not and
Authentication. It is generally used for encrypted communication between
servers and web apps, like a web browser loading a website, it can also be used
for encryption of messages, emails, VoIP.
Web server and its types:
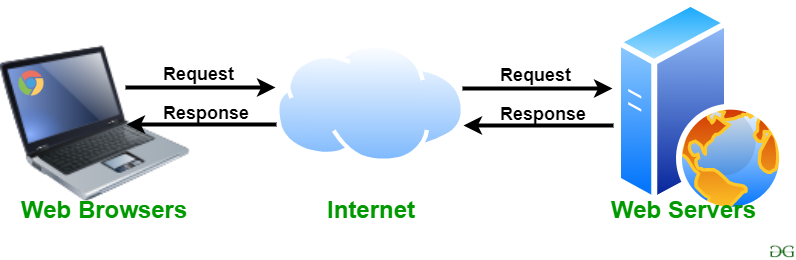
There are many web servers available in the market both free and paid. Some of them are described below:
- Apache HTTP server: It is the most popular web server and about 60 percent of the world’s web server machines run this web server. The Apache HTTP web server was developed by the Apache Software Foundation. It is an open-source software which means that we can access and make changes to its code and mold it according to our preference. The Apache Web Server can be installed and operated easily on almost all operating systems like Linux, MacOS, Windows, etc.

- Microsoft Internet Information Services (IIS): IIS (Internet Information Services) is a high performing web server developed by Microsoft. It is strongly united with the operating system and is therefore relatively easier to administer. It is developed by Microsoft, it has a good customer support system which is easier to access if we encounter any issue with the server. It has all the features of the Apache HTTP Server except that it is not an open-source software and therefore its code is inaccessible which means that we cannot make changes in the code to suit our needs. It can be easily installed in any Windows device.

- Lighttpd: Lighttpd is pronounced as ‘Lightly’. It currently runs about 0.1 percent of the world’s websites. Lighttpd has a small CPU load and is therefore comparatively easier to run. It has a low memory footprint and hence in comparison to the other web servers, requires less memory space to run which is always an advantage. It also has speed optimizations which means that we can optimize or change its speed according to our requirements. It is an open-source software which means that we can access its code and add changes to it according to our needs and then upload our own module (the changed code).

- Jigsaw Server: Jigsaw has been written in the Java language and it can run CGI (common gateway interference) scripts as well as PHP programs. It is not a full-fledged server and was developed as an experimental server to demonstrate the new web protocols. It is an open-source software which means that we can access its code and add changes to it according to our needs and then upload our own module (the changed code). It can be installed on any device provided that the device supports Java language and modifications in Java.

- Sun Java System: The Sun Java System supports various languages, scripts, and technologies required for Web 2.0 such as Python, PHP, etc. It is not an open-source software and therefore its code is inaccessible which means that we cannot make changes in the code to suit our needs.

How does a virtual private network (VPN) work?
A VPN extends a corporate network through encrypted connections made over the Internet. Because the traffic is encrypted between the device and the network, traffic remains private as it travels. An employee can work outside the office and still securely connect to the corporate network. Even smartphones and tablets can connect through a VPN.










Comments
Post a Comment